The management of our Ruby on Rails application secrets (things such as service credentials and the secret_key_base) belongs to one of the most prioritized list. Rails 5.1 introduced Encrypted Secrets to help simplify the management of our application secrets in Ruby on Rails. It will make easier to keep secrets more secret: developers can encrypt secrets inside the source code so that they are only available inside the running application process. This is not a problem because Ruby on Rails includes some sophisticated helper methods, such as against SQL injection.
Why encrypted secrets in Ruby on Rails?
Ruby on Rails is a full-stack framework. It ships with all the tools needed to build amazing web apps on both the front and back end. As one of the most powerful ways to quickly develop web applications, Ruby on Rails has a high relevance and demand in today’s marketplace. This blog intends to provide quick Ruby on Rails security tips for developers.
Since Rails 4.1, the framework has given us the ability to centrally store secrets in the config/secrets.yml file. The glaring shortcoming of secrets.yml is that the file actually is in no way secure, and we cannot actually safely check it into version control with any production credentials. The convention for production credentials was always to load them within secrets.yml but from the host environment. Usually secrets file in the Ruby on Rails environment would end up looking something like this:
development:
secret_key_base: 972888f3521e5c5ec8491cd3295e51af38fc93e059c1a00e8e03804288f64d77753b66a5108baaddfe6
some_api_key: 055ef473d6df1055
test:
secret_key_base: 1d1be5ad7ea1e9d833e752a2de941217222fe9c6ea5467b9d63f69d38c8aa4c4219db9edc37d3b80fc4
some_api_key: 055ef473d6df1055
production:
secret_key_base: <%= ENV["SECRET_KEY_BASE"] %>
some_api_key: <%= ENV["SOME_API_KEY"] %>
Rails 5.1+’s Encrypted Secrets feature can now keep production secrets in a second fully encrypted file (AES-256 by default), which is managed by the framework. Secrets from the encrypted secrets.yml.enc file are merged with secrets from the unencrypted secrets.yml file.
Getting started with Encrypted Secrets in Ruby in Rails :
To see this in action as of 5.1.0.beta1:
gem install rails -v 5.1.0.beta1
rails new testsekrets
cd testsekrets
The generated scaffolding includes a config/secrets.yml for storing unencrypted secrets. Encrypted secrets is not set up by default, and in order to bootstrap it you need to run:
bin/rails secrets:setup
After running code, we will get :
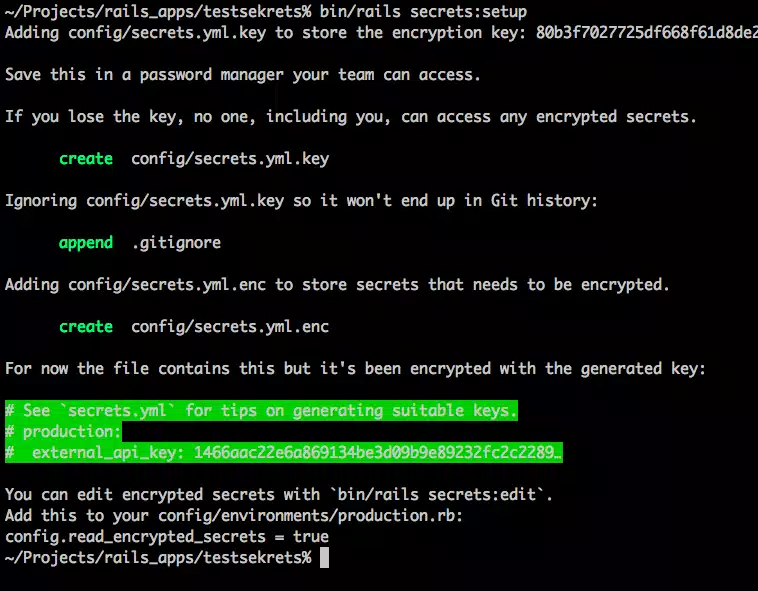
This will drop a few files into our project tree:
- config/secrets.yml.key – contains the actual secret key used by the framework to AES-encrypt your secrets.
- config/secrets.yml.enc – the encrypted digest form of your (encrypted) secrets.
As per the instructions, we need store the one-time generated encryption key in 1password, or vault, or wherever just our team shares secrets. We should not lose the key. Generally, developers of the application can either:
- Place this key in config/secrets.yml.key; or
- Set env var RAILS_MASTER_KEY to this value
It is the latter that we will also use when deploying to production.
To edit your secrets, invoke the command:
Ruby on Rails deployment to production For Sublime:
EDITOR=subl bin/rails secrets:edit
Ruby on Rails deployment to production for Vim:
EDITOR=vim bin/rails secrets:edit
The secrets:edit task will decrypt secrets and pop them open in editor where we can make changes. When we quit the editor, the framework will re-encrypt the secrets and overwrite the existing secrets.yml.enc file.
Usage in production
Ruby on Rails provides an excellent development ecosystem for building high performing web applications. In production, Rails will look for the decryption key either in the environment variable RAILS_MASTER_KEY or in a local copy of the key file (config/secrets.yml.key). How we get the environment variable exposed to our application or how we inject the key file is a matter that is specific to our particular hosting and infrastructure management setup.
Final Words
Gurzu is a Ruby on Rails company based in Nepal. Here at Gurzu we transform ideas into world-class products. Our professional team is fluent in 3Rs (Ruby on Rails, React and React Native). We’re ready to design, build and develop something that your users will love. We love building web applications and do so with extreme passion and craftsmanship.
Ruby is a dynamic, high-level, general-purpose programming language known for its simplicity and productivity.Explore our awesome projects on Ruby .
Need a team of expert Ruby developers for your next big project? Hire the best team of developers from Gurzu. Book a free consultation call with us today to learn more!

